Projects
I always have a side project that I’m working on (usually more than one). I’ve highlighted some of the major public ones here, but you can probably find newer info on my GitHub/GitLab profiles.
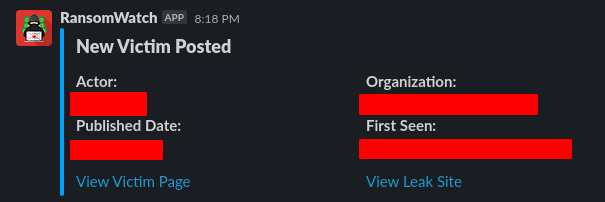
RansomWatch
RansomWatch is a tool that helps cyber threat intelligence (CTI) analysts monitor ransomware leak sites. It scrapes various ransomware leak sites to identify new and removed victims, and sends notifications via Slack when something changes.
Technologies used: Python, sqlite, Docker
ORTSOC Infrastructure
This project was a part of my senior design/capstone course at Oregon State University, where I lead a team of five to develop the infrastructure for the Oregon Research & Teaching Security Operations Center (ORTSOC), an experiential learning SOC that will employ students to help monitor customer networks and defend against cyber intrusions. The infrastructure uses the Elastic Stack, nginx, wireguard, BIND9, and a few other components to provide the basic building blocks. I personally worked on the overall system architecture, and helped build playbooks for DNS, Elasticsearch, and NTP. I also helped design and deploy the physical infrastructure running VMware to support the project.
Technologies used: Ansible, VMware
Homelab
I have a homelab (running VMware) where I learn about different IT technologies, and run the infrastructure for my malware analysis and other personal projects. Check out my latest blog post for details on Lab 3.0.
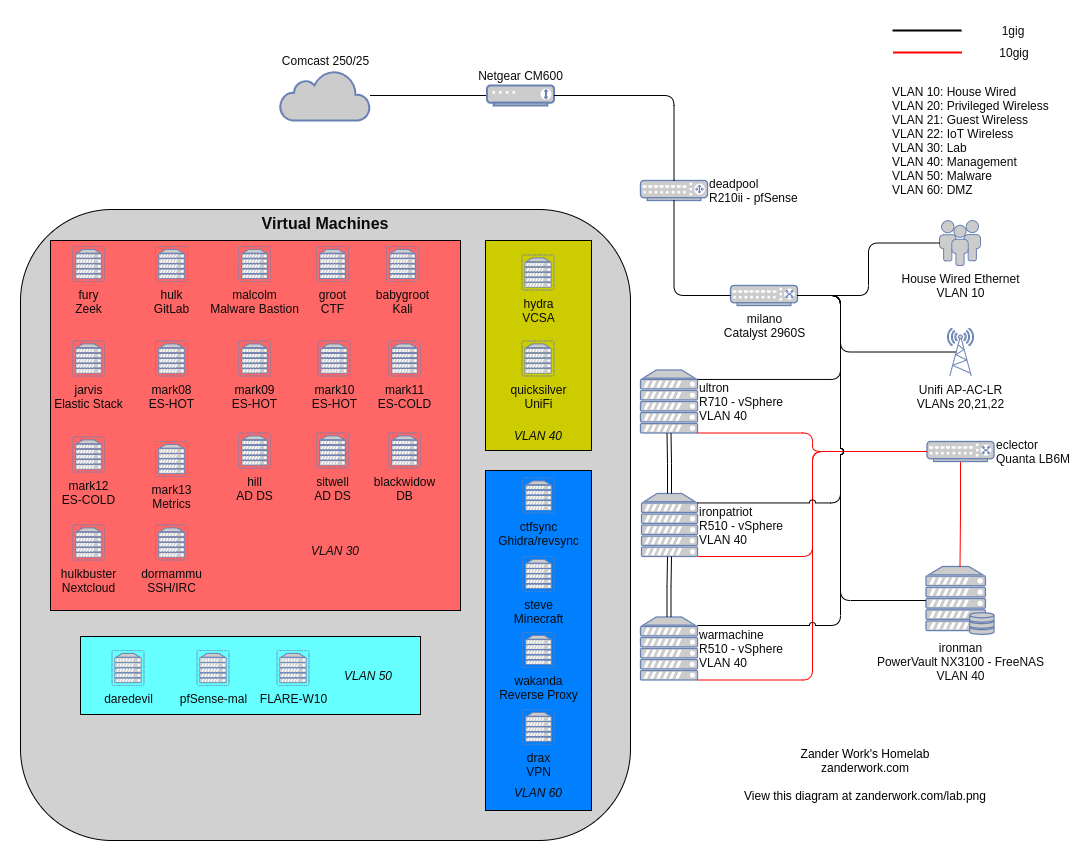
Latest lab diagram (Lab 3.0)
TrainWatch
TrainWatch is an iOS and watchOS app that monitors the status the subway trains in Washington, D.C. and provides a clean interface on your wrist for checking when the next trains will arrive nearest you.
Technologies used: Xcode, Swift, SwiftUI
Zeek Packages
As an active Zeek user, I often find myself identifying gaps in coverage by the existing functionality. In these situations, I always try and build a package to implement this functionality, and share it with the rest of the Zeek community.
I’ve written/published two packages so far, and hope to do more in the future:
- zeek-intel-path
- This package adds a new Intel type for URL paths.
- zeek-bogon
- This package adds detection for bogon networks, and adds a new field to the
conn.logthat can be used to filter for them. - It was also the winner of the third Zeek Package Contest.
- This package adds detection for bogon networks, and adds a new field to the
You can see an up-to-date list of all my published package by checking the package listings.
massmoji
massmoji is a tool that downloads all of the 10,000+ emojis from Slackmojis and automatically adds them all to your Slack workspace. Functionality of this will break whenever Slack changes their API on the web interface, as this uses a private API route that was identified from monitoring the HTTP traffic of manually uploading an emoji. However, it works pretty fantastically for the time being.
Technologies used: Python
Decompliation as a Service (DaaS)
DaaS is a REST API that enables someone to upload a binary and utilize the IDA Pro decompiler to decomplie the binary, and retrieve the output pseudo-C over HTTP. It was developed to support the OSUSEC Discord Bot, which now has a !decompile command.
Technologies used: Python, Flask, sqlite, Docker, IDA Pro
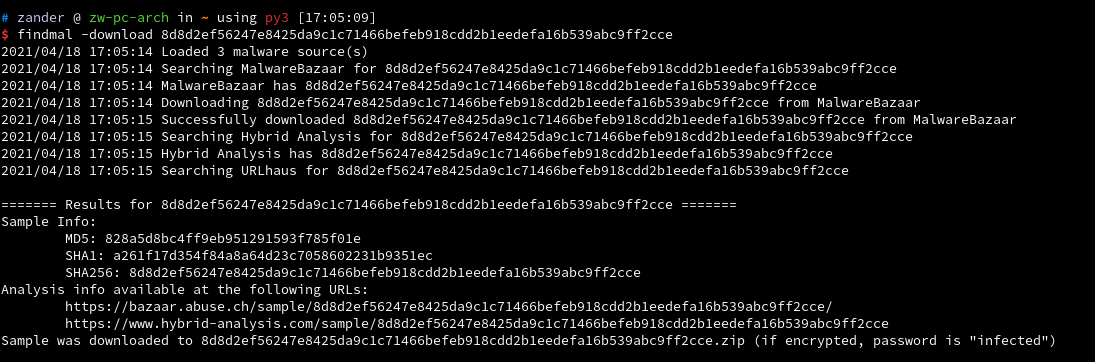
findmal
findmal is a CLI tool that makes it easier to download malware samples. Provide one or more hashes, and it checks different malware repositories to find the sample and download it. I use it regularly when I stumble across a tweet or article that mentions a hash, so I can pull down the sample and save it for my own analysis.
Technologies used: Go
DamCTF
DamCTF is a Capture the Flag competition hosted by the OSU Security Club. I was the lead organizer and infra team lead for 2020, and developed a full CI/CD pipeline that handled all of our challenges and infrastructure deployments, along with monitoring the health of our infrastructure. The infrastructure was backed by Ansible and Terraform for Infrastructure-as-Code (IaC), and operated primarily using Google Kubernetes Engine on the Google Cloud Platform (GCP; they were one of the event sponsors).
I also developed a 5-part malware analysis challenge, which involved participants analyzing PCAP traffic, reverse engineering a Linux malware sample, building an emulator for the C2 traffic, and exploiting a web panel. For more details on this challenge, see this blog post.
For the infra components, I worked with these technologies:
- Ansible
- Terraform
- GitLab CI/CD
- Docker
- bash
- Elastic Stack
- Google Cloud
- Kubernetes
For the challenges I authored:
- C
- Docker
- Python
- PHP
- MySQL
Public challenge git repo (the infra repo isn’t public, happy to share info about this on request)
Discord Webhook Proxies
For DamCTF, I wanted to integrate our monitoring and CI/CD pipeline into our existing communications platform (Discord), I built two proxies that ran in our k8s cluster that handled formatting rich embed messages for Discord based on incoming data from various sources:
Technologies used: Go, Docker
Docker Zeek + ELK
This project provides a simple way to quickly deploy Zeek and the Elastic Stack using Docker for one-off PCAP analysis. Using docker-compose, you can quickly spin up all of the necessary infrastructure, and drop PCAPs in a folder being watched by Zeek. After they are analyzed, you can query the output Zeek data in Kibana.
Technologies used: Docker, Zeek, Elastic Stack, bash
OSU Security Club WiFi Demo
This was a project put together for the 2019 College of Engineering Expo to show the dangers of using untrusted WiFi networks.
There are two parts to the demo:
- Passive collection: The user enters some data on the webpage, and the attacker machine passively captures all of the form fields
- Active MitM: The user enters some data on another webpage, and the attacker machine intercepts the request and modifies some fields to show they were able to actively interrupt the connection

Flagnado
Flagnado is a CTF attack/defense dashboard and exploit throwing tool. It allows team members to upload their exploits and automatically run them against the target hosts throughout the competition, and tracks their success against each team.
Technologies used: Python, Django, sqlite